In the day-to-day operations of any organization, Excel files are an essential tool for managing information. They contain everything from client lists and employee payroll to critical financial data. To secure these files, the most common practice is to use a password. However, is this measure truly secure?
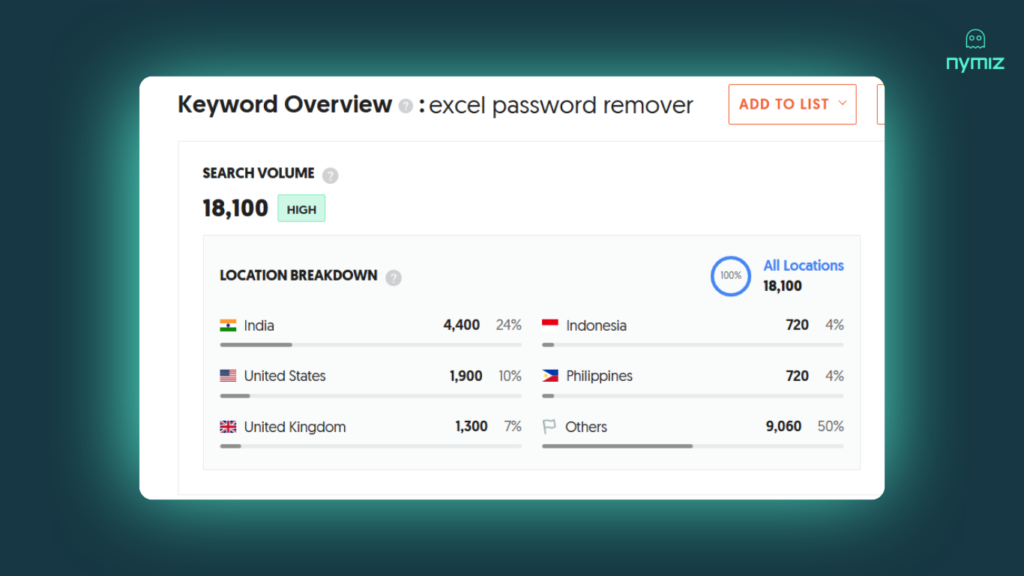
The data reveals a disturbing reality. Every month, there are over 18,000 Google searches for the term “Excel Password Remover.” The existence and popularity of these tools, which can bypass a file’s protection in seconds, show that a password is a fragile barrier for your company’s most valuable information.
In this article, we’ll analyze why relying on passwords represents an operational and legal risk and explore the definitive solution to robustly protect your data.
Why an Excel data breach puts your organization at risk
When the security of an Excel file is compromised, it’s not just a document that gets exposed; it triggers a chain of consequences that can severely impact you financially, legally, and reputationally.
What critical data lives (and is at risk) in your spreadsheets?
Before assessing the risk, it’s crucial to be aware of the information we store. These files often house an organization’s most confidential data:
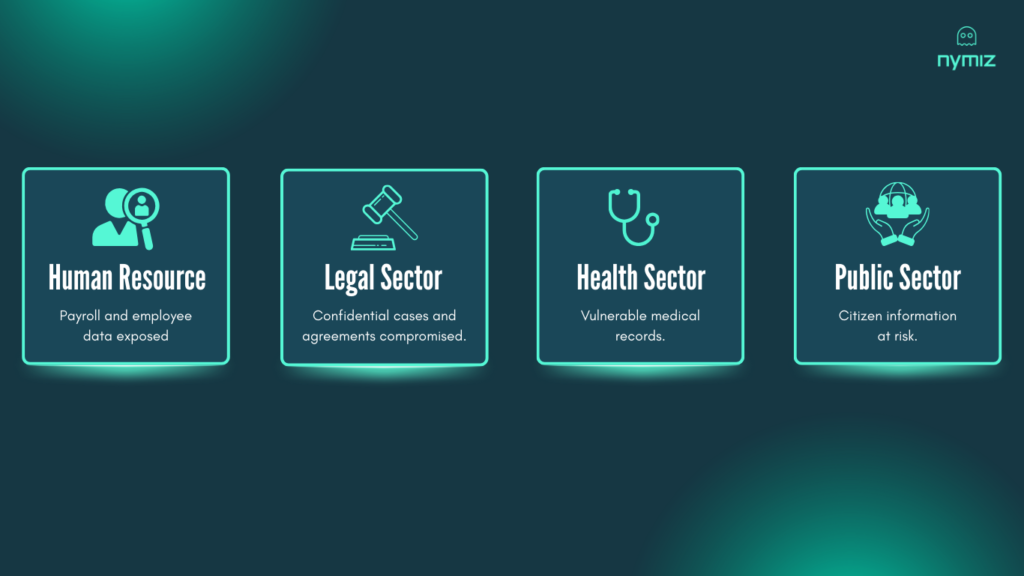
- Human Resources: Complete employee lists with national IDs, social security numbers, salaries, bank accounts, medical leave history, and performance reviews. A leak of this information not only violates privacy but can also create serious internal conflict.
- Legal Sector: Client files detailing cases, witness identities, confidential settlements, and legal strategies. Their exposure can fatally compromise a client’s position and the firm’s reputation.
- Healthcare Sector: Databases with clinical histories, diagnoses, genetic test results, and insurance information. This is especially sensitive data, and a leak can be devastating to a patient’s privacy.
- Public Sector: Census data, lists of aid beneficiaries, administrative records, and tax information. The administration has a duty to protect this citizen data with the highest guarantees.
When a “simple Excel file” becomes a million-dollar crisis
These consequences are not theoretical. They are documented in real-world incidents and industry reports.
- The Financial Impact: According to the 2024 Cost of a Data Breach Report from IBM, the average global cost of a data breach has reached $4.45 million.
- The Human Factor as a Trigger: Verizon’s 2024 DBIR reveals that 68% of security breaches involve a human element.
- The Police Service of Northern Ireland (PSNI) Case: A clear example was the accidental leak of an Excel file containing the personal data of over 9,400 officers.
The legal perspective: What does the GDPR say about your file security?
Relying on a simple Excel password isn’t just poor security practice; it’s a very difficult position to defend under the General Data Protection Regulation (GDPR). The regulation doesn’t explicitly mention Excel, but its core principles directly address why this method is insufficient.
Article 32: Security of processing and “appropriate Ttechnical measures”
The GDPR requires organizations to implement “appropriate technical and organizational measures to ensure a level of security appropriate to the risk.” What is considered “appropriate” depends on the data’s sensitivity. For a file with names and emails, the risk is high; if it contains health or financial data, it’s critical.
A password that can be removed with publicly available tools (as the 18,000 monthly searches for “Excel Password Remover” prove) cannot be considered an “appropriate” technical measure. In an audit or a data breach, it serves as evidence of a lack of diligence.
Article 25: Data protection by design and by default
This principle requires privacy to be integrated into systems and processes from their inception, not as an afterthought. Protecting a payroll list with a password is a patch, not a solution designed to be secure. “By default” means the system must be secure in its initial configuration, and an un-anonymized Excel file is not. Anonymization, in contrast, is the perfect example of data protection by design: security is built into the data itself.
Article 5: The “integrity and confidentiality” and “accountability” Principles
The GDPR states that personal data must be “processed in a manner that ensures appropriate security, including protection against unauthorized or unlawful processing and against accidental loss, destruction or damage.”
Furthermore, the “accountability” principle requires the data controller not only to comply with the regulation but also to be able to demonstrate it. If an Excel file breach occurs, you will have to provide evidence of the security measures you had implemented. Presenting a password as your only barrier would, in practice, be an admission of negligence that could lead to the highest penalties.
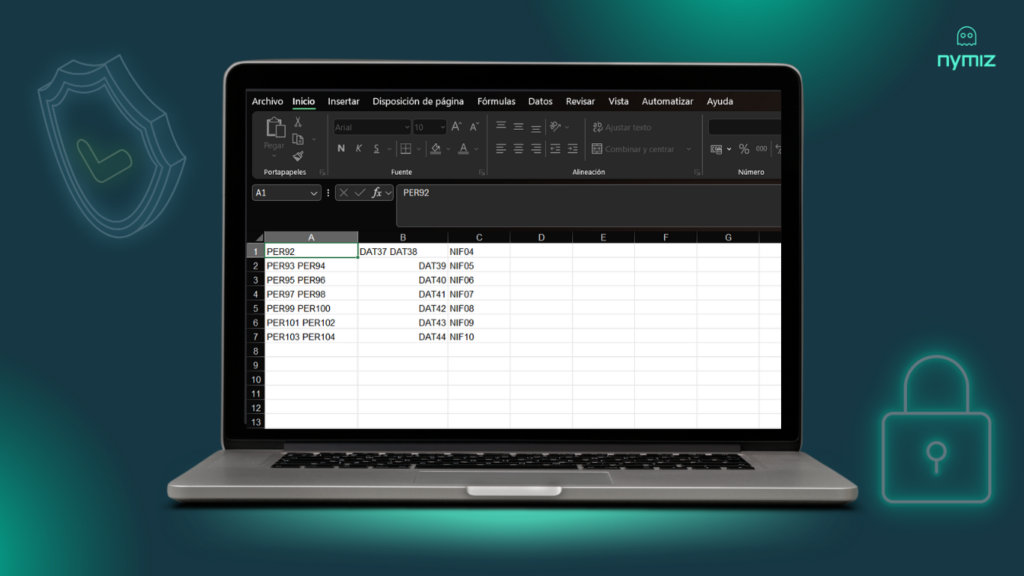
The contrast: Manual risk vs. automated security
Beyond a potential breach, the way we protect files directly impacts day-to-day productivity and security.
The real consequences of password protection
- Constant risk exposure: The original data is always present in the file. A human error, unauthorized access, or a moment of carelessness in sharing is all it takes to expose all sensitive information.
- Wasted time and broken workflows: Manually managing passwords (creating them, sharing them securely, remembering them) is inefficient, disrupts collaboration, and creates bottlenecks.
- A false sense of security: Teams operate believing their data is safe, which encourages risky practices like sending confidential files through insecure channels.
- Use of insecure applications: When a password is forgotten, employees often turn to online “password recovery” tools, uploading the confidential file to third-party servers with no security oversight.
The immediate benefits of anonymization

- Automation and time savings: Anonymization integrates automatically into your workflow, eliminating manual password management and saving hours of work.
- Confidence to collaborate and share: It allows you to share data with complete peace of mind, knowing it’s technically impossible to expose personal information, whether internally or externally.
- Security from the start: The data is protected by design. The risk isn’t managed; it’s eliminated at the source before the file is ever shared.
- Drastic risk minimization: By removing identifying data, the risk of a data breach and its severe legal and financial consequences is minimized.
The real solution: Protect the data, not just the file
If a password is an insufficient barrier, the solution requires a fundamental shift in focus: instead of trying to protect the container (the file), we must protect the content itself (the data).
This is the principle of intelligent anonymization.
It’s a process that irreversibly transforms personal data into fictitious data or tokens. Crucially, while the identity is removed, the analytical value of the data remains intact. The structure, format, and consistency of the information are preserved so you can continue to work with it.
Our anonymization is intelligent because it’s powered by AI algorithms capable of understanding the data’s context to apply the most suitable technique. This level of security enables advanced use cases, such as ensuring data privacy when training Machine Learning and LLM models safely.

Anonymization use cases by professional sector
Anonymization solves critical problems in daily professional life:
For the Legal Sector: It allows a law firm to share case files with external experts for analysis, completely hiding the identities of clients, witnesses, or other parties.
For Human Resources: It facilitates the creation of reports on salary gaps, equality, or diversity for management or committees without exposing any employee’s personal or salary data.
For the Healthcare Sector: It enables research centers to analyze thousands of medical records for epidemiological studies while guaranteeing patient privacy at all times.
For the Public Sector: It allows administrations to publish data on transparency portals for statistical analysis (open data), complying with the law without exposing citizens’ personal information.
Excel file anonymization with Nymiz
Thanks to an AI technology that ensures 95% accuracy in data detection and saves up to 80% of the time compared to manual methods, applying robust anonymization is a quick and intuitive process.
Step 1: Securely upload your file
Upload or drag and drop your Excel file into the Nymiz platform. The entire process takes place in a secure and encrypted environment.
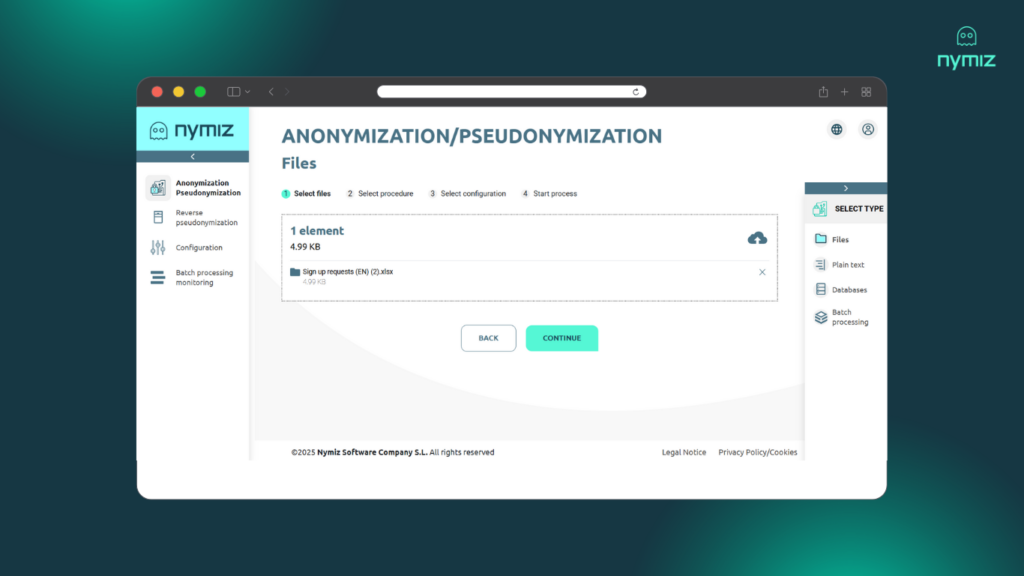
Step 2: Automatic and intelligent detection
Our AI algorithms analyze the document and automatically identify all personal data, such as names, national IDs, addresses, etc
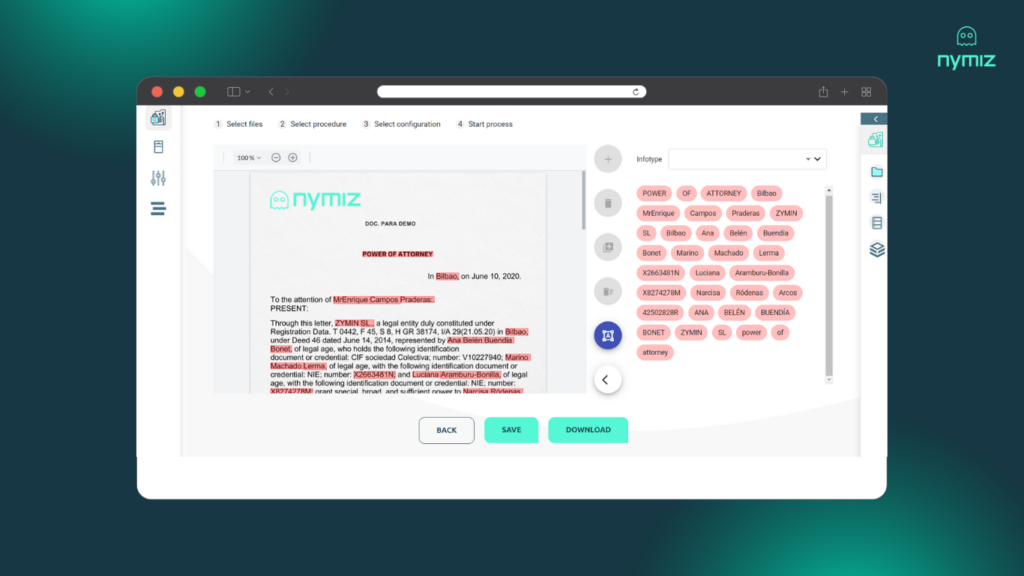
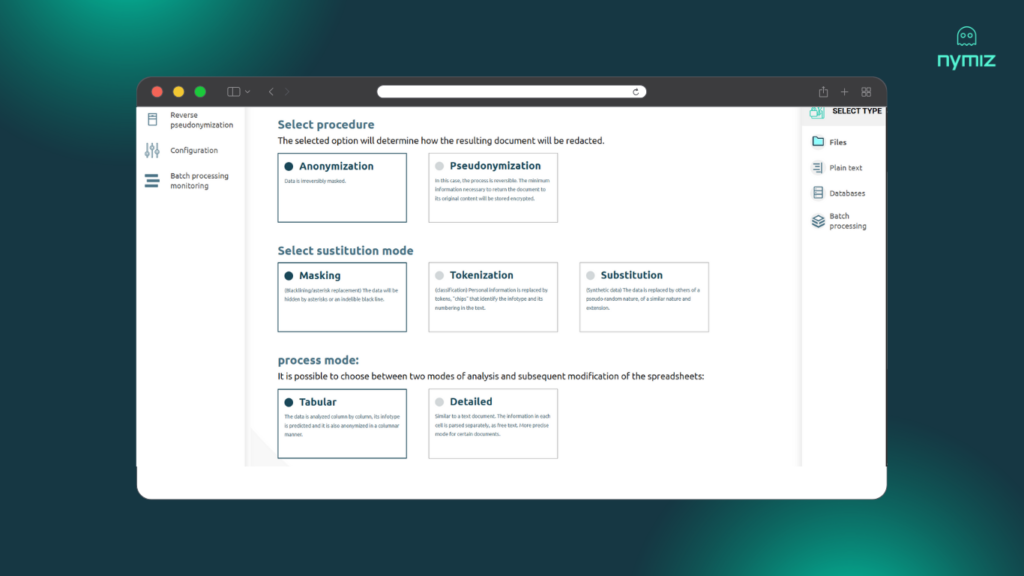
Step 3: Choose your anonymization technique
The platform allows you to choose the most appropriate technique for your use case, from replacement with asterisks to tokenization or the generation of synthetic data
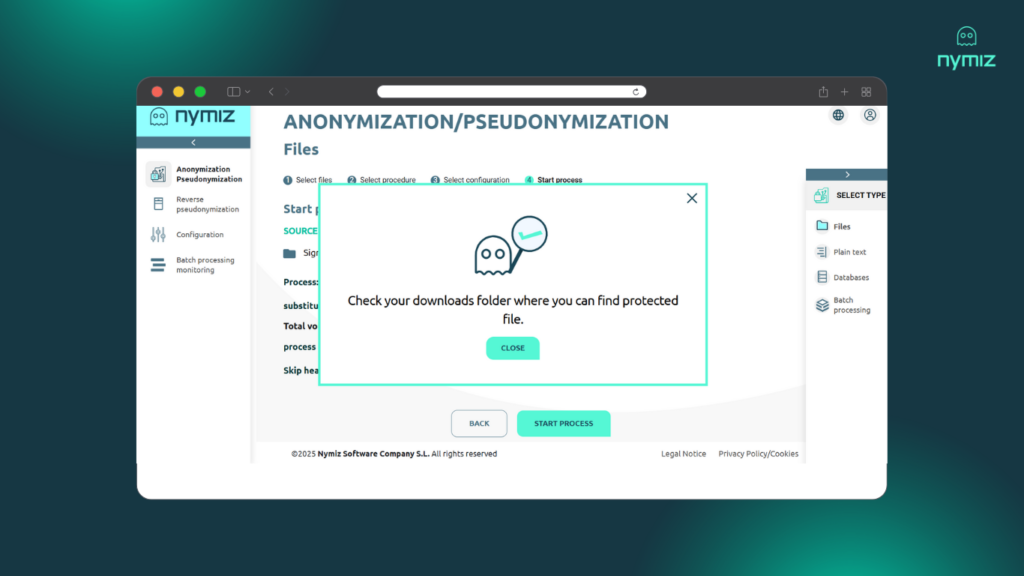
Step 4: Download the protected file
In seconds, the file is processed. Download the new version, completely anonymized and safe to be shared, analyzed, and used without risk.
A Final thought: From protection to innovation
In the age of Big Data and Artificial Intelligence, an organization’s value lies in its ability to use data ethically and securely. Anonymization is no longer just a regulatory compliance measure; it has become a strategic advantage.
This isn’t just about avoiding a fine; it’s about building a culture of trust and enabling the future. Protecting data doesn’t mean locking it away; it means giving it the freedom to be used intelligently and safely, opening the door to innovation.
Take the next step toward real security
Reading about the problem is the first step. Seeing the solution in action is what truly makes a difference.
Want to see a live demonstration of how we can anonymize one of your Excel files in seconds? Book a free demo with us and discover how to protect your data for good.
Frequently Asked Questions (FAQ)
Is the data still useful after being anonymized?
Yes, completely. Unlike simple deletion, advanced anonymization techniques preserve the data’s structure, format, and statistical value. This allows for accurate analysis and valid conclusions with zero risk to privacy.
Is anonymization the same as pseudonymization?
No, and the difference is crucial, both legally and technically. Pseudonymization replaces personal data with pseudonyms but allows for re-identification with additional information. Anonymization, on the other hand, is an irreversible process that eliminates any possibility of re-identifying an individual, offering the highest level of protection.






