For years, organizations have strengthened their internal defenses, convinced that the danger was beyond them. But the landscape has changed.
Today, third-party cyberattacks are the new gateway to the heart of businesses. Cybercriminals no longer seek to directly attack large corporations, but rather infiltrate through suppliers, agencies, and technology partners that handle sensitive information.
From a technology consulting firm in Berlin to a marketing agency in Lima to a SaaS provider in New York, the trend is global: 82% of data breaches involve third parties (IBM Cost of a Data Breach 2024).
And with the emergence of artificial intelligence (AI), the landscape has become even more complex: attacks are faster, more precise, and harder to detect.
A recent case that reflects a common reality
In October 2025, Mango, one of the largest companies in the European textile sector, confirmed unauthorized access to customer personal data by one of its third-party suppliers.
The attackers accessed names, email addresses, phone numbers, and postal codes used in marketing campaigns. Although the company acted transparently—notifying the Spanish Data Protection Agency (AEPD), contacting those affected, and activating its security protocols—this case serves as a reminder that no company is completely safe if its partners aren’t. Third-party cyberattacks can affect even organizations with robust internal protection systems.
The risk increases every time data is shared with agencies or integrators without adequate privacy infrastructure.

Global breaches that set a trend
The Mango incident is just one of many recent examples.
In recent years, digital supply chains have become the primary target for attackers.
- SolarWinds (USA): Its software compromised more than 18,000 organizations, including government agencies.
- MOVEit (Global): More than 60 million people were affected after a vulnerability was exploited in an external service.
- Banco Santander (Spain): A third-party compromise caused the data breach of 30 million people.
- Capita (UK): The UK data watchdog has fined the company £14 million for the data breach in which hackers stole the personal information of more than 6 million people.
According to CCN-CERT, Spain recorded 97,348 cybersecurity incidents in 2024, a 16.6% increase over the previous year.
More than a third were related to cyberattacks on third parties or external integrations.
ENISA (European Agency for Cybersecurity) confirms the trend: 54% of large European organizations consider third-party risk their primary concern.
When AI boosts attack sophistication
Artificial intelligence has transformed productivity… and so has crime.
Attackers are using AI to automate phishing attacks, generate deepfakes, and analyze large volumes of stolen data.
But the most disturbing trend is that some ransomware groups are training AI models with leaked data, thereby improving their attack tactics and personalizing extortion attacks.
In sectors such as healthcare, legal, and financial services, this translates into new threats:

The weakness of digital supply chains
Every company is part of an interconnected network of partners, agencies, integrators, and cloud services. This interdependence, while driving efficiency, multiplies entry points for attackers.
Common vulnerabilities in suppliers
- Shared access without traceability.
- Unencrypted networks or devices.
- Outsourcing without security controls.
- Lack of segmentation of sensitive data.
Third-party cyberattacks exploit this complexity to infiltrate undetected. Security no longer depends solely on an organization’s perimeter, but on its entire extended network of trust.
The regulatory framework is strengthened
The increase in third-party cyberattacks has changed the way regulators understand security: it is no longer enough to protect what is owned; now we must also protect what is connected. In this new reality, cybersecurity is no longer delegated: it is shared.
Governments and international organizations are responding with more demanding regulatory frameworks that reinforce shared responsibility between organizations and suppliers. Globally, this trend is redefining the way companies must design, audit, and operate their data systems.
Europe: Security throughout the supply chain
Europe has been a pioneer in shaping a privacy-as-operational-infrastructure model. With the entry into force of NIS2, organizations in essential sectors—such as healthcare, energy, public administration, and digital services—are required to extend their security controls to the entire supply chain. This involves auditing critical suppliers, ensuring incident traceability, and establishing continuity protocols that extend beyond the main company.
The DORA Regulation, focused on the financial sector, takes this vision a step further. It requires banks and institutions to manage their suppliers’ technological risk with the same rigor as their own, including periodic audits, contingency plans, and specific contractual clauses to ensure oversight of third-party technology providers.
For its part, the General Data Protection Regulation (GDPR) remains the A benchmark in Europe. It introduces the principle of accountability—or proactive responsibility—and promotes measures such as anonymization or pseudonymization to reduce the impact of potential breaches and facilitate regulatory compliance, even in interconnected environments.
United States: From compliance to resilience
In the United States, the focus is on strengthening cyber resilience rather than imposing punitive frameworks. Organizations such as CISA and NIST have updated their guidelines so that companies integrate security by design and by default, especially when they rely on third-party or cloud infrastructures.
The NIST Cybersecurity Framework (CSF 2.0) and the Third-Party Risk Management guidelines establish clear recommendations: identify critical dependencies, assess shared vulnerabilities, and continuously monitor vendor performance.
At the industry level, regulations such as HIPAA (in healthcare), GLBA (in financial services), and the new SEC guidelines require organizations to report security incidents in a timely manner and ensure that their partners meet the same protection standards as they do. This evolution marks a cultural shift: transparency and collaboration are becoming the new standard of digital trust.
Latin America: Expanding shared responsibility
In Latin America, personal data protection and cybersecurity are undergoing an accelerated maturation process. Countries such as Brazil, with its General Data Protection Law (GDPR), have established a framework similar to the European one that reinforces the obligation of data processors and data controllers to adopt robust technical and organizational measures.
Other countries such as Mexico, Chile, and Colombia are moving toward shared responsibility models between companies and technology providers, integrating security requirements into contracts and reinforcing the obligation to report incidents to the competent authorities.
As these regulations become more established, there is also a growing awareness that privacy cannot depend on trust, but rather on architecture. Designing privacy at the source becomes the only sustainable way to protect data in distributed ecosystems.
Taken together, these regulations mark a turning point: privacy and cybersecurity are no longer isolated legal requirements, but structural components of responsible innovation.
Companies that integrate data protection by design—as Nymiz does—will not only reduce risk but will also gain the confidence necessary to innovate frictionlessly in the era of artificial intelligence.
What companies can do to reduce risk
Third-party risk management requires a dual approach—contractual and technical—but the real leap forward comes when you design privacy at the source and ensure traceability for every access. Here’s a practical checklist to get started today:

Nymiz helps you integrate privacy throughout the entire workflow, not at the end.
At Nymiz, we believe that privacy doesn’t slow down innovation, but rather drives it when it becomes infrastructure. Our platform offers advanced anonymization and built-in traceability, allowing data to flow securely and compliantly between companies and third parties.
How we do it in 3 steps:
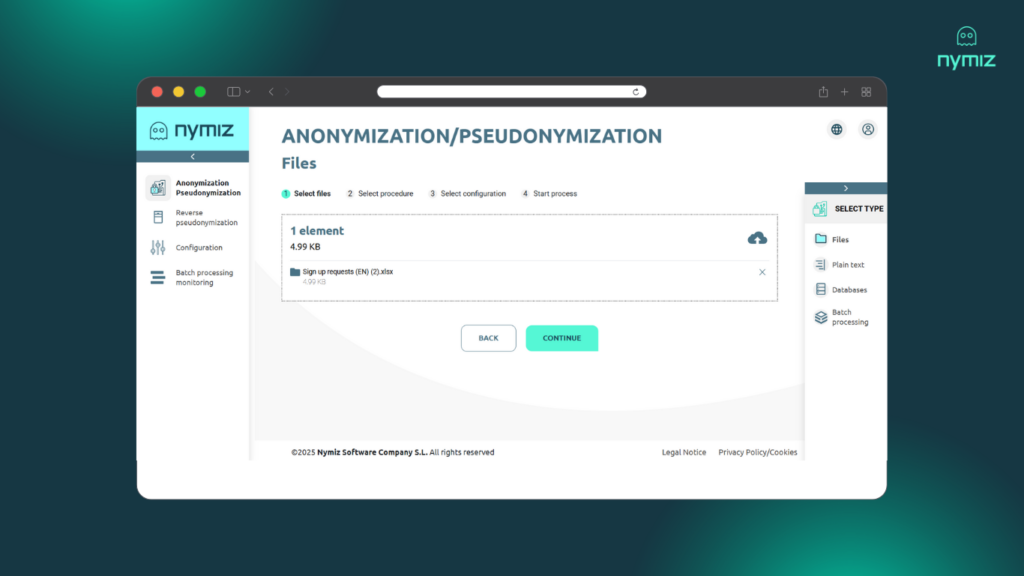
- Upload the documents you need to anonymize and choose the method that best suits your use case.
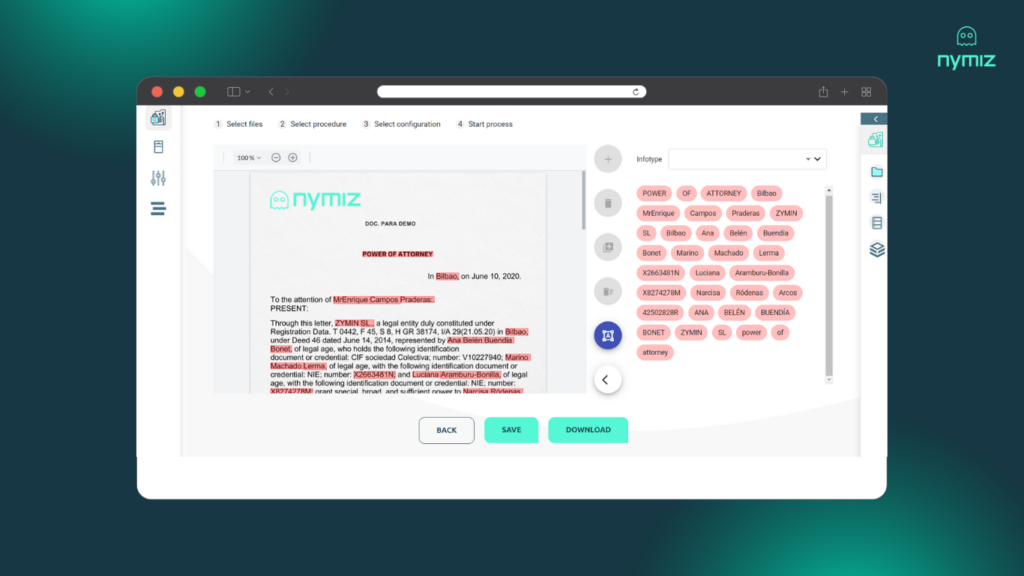
2. Nymiz identifies sensitive data by context (structured and unstructured documents) and anonymizes it while maintaining data structure and consistency (with infotypes and exceptions for your internal codes).
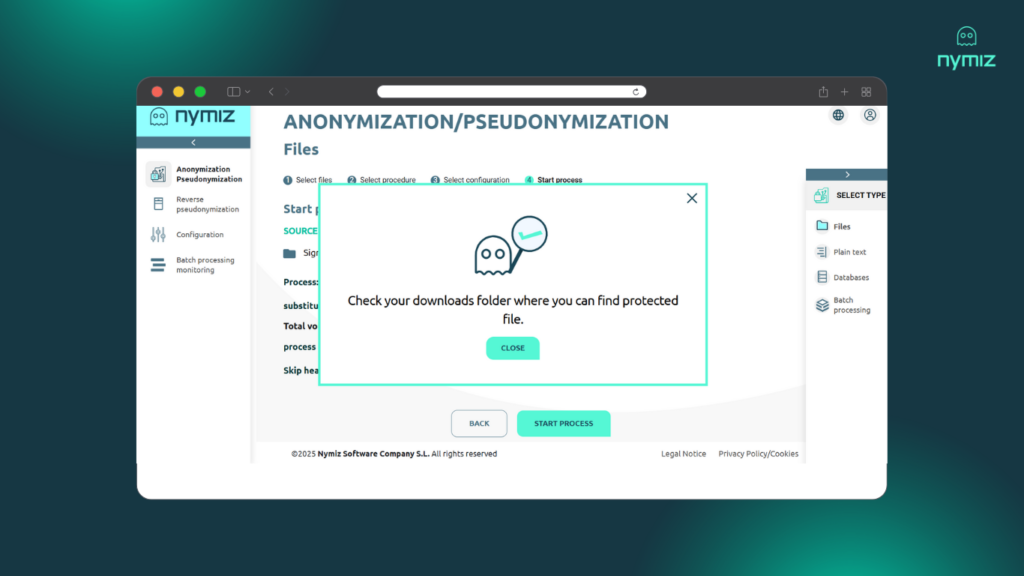
3. Review that all parameters are in order and complete the process. Once completed, it will be ready to download and share with your partners (agencies, SaaS), without moving data outside your environment.
Nymiz turns privacy into operational infrastructure so you can share data with third parties securely, usefully, and compliantly.
Book a demo and tell us about your use case.
Conclusion: Proactive is the new defense
The current landscape demands a shift from reaction to prevention. Third-party cyberattacks will continue to grow, but their impact can be reduced if privacy is designed from the ground up.
True security isn’t about closing doors, but about intelligent data sharing. Nymiz helps companies protect what matters most: trust. Because privacy is no longer an option, it’s the foundation of innovation.






